
GoITWay is a provider of software consulting and packaged systems implementation services.Our expert team of software engineers and professionals are extremely adept in creating customized business applications.Our wide range of technology experience strengthens our existing service spectrum and defines our credentials as an enterprise-class solution provider.GoITWay provides a wide range of services along with complete business process management.
Monday, 26 November 2018
Tuesday, 20 November 2018
INTEL TO UNVEIL NEW HASWELL CHIPS IN SEPTEMBER
Intel's Haswell chips have been quite well-recieved. According to DigiTimes, Intel will be expanding its Haswell line-up with new processors in September. The report states that the company will be unveiling 13 new processors for desktops and 24 for notebooks.
Intel has separated its mobile processors in several categories, which includes the M series mainstream chips, H series high-performance chips and Y and U series for low power-consumption chips.
Despite its expansion of Haswell, Intel won't be abandoning its previous-generation Ivy Bridge chips. The company will be bringing out four Ivy Bridge chips in September. The company is also expected to unveil its Bay Trail T platform chips for tablets, M platform for entry-level notebooks and D platform for entry-level desktops.
Intel had launched its Haswell chips back in June. In contrast to the buzz regarding the launch, Intel has made relatively modest microarchitecture improvements with Haswell, especially when compared to Sandy Bridge and Ivy Bridge release, which is the name given to 22nm shrunk die of the Sandy Bridge microarchitecture based on 3D transistors.
The release was in line with Intel’s ‘tick-tock’ product development and release strategy adopted since 2007. Every 'tick' is a shrinking of process technology of the previous microarchitecture and every 'tock' is a new microarchitecture. Intel’s Sandy Bridge microarchitecture, introduced in early 2011, was a ‘tock’ built using a 32nm manufacturing process, the Haswell release too is a ‘tock’ and it uses the 22nm manufacturing process as Ivy Bridge.
GoITWay
Monday, 29 October 2018
Data & cyber security may come under Trai, Telecom Commission
MUMBAI: The remits of the telecom regulator and the Telecom Commission are in the process of being widened that may see them overseeing issues such as data privacy, security and cybercrime, which are currently being looked into by the IT ministry, people familiar with the matter said.
According to officials in the Department of Telecommunications and the Telecom Regulatory Authority of India (Trai), these changes, which will come through an amendment in laws, underline the fact that consumers access most of their data via mobile phones, and hence the telecom department will need to get involved.
“We have to realise that subjects such as data privacy and security all flow through the telecom network. In fact, 93% of all such data is consumed on telecom networks, for example ecommerce, etc,” said a senior government official, who did not want to be named.
“Aspects of data privacy etc should all come under one ambit, and that should be the Digital Commission and the Digital Communications Regulator,” the official said.
Any change in the regulatory ambit of one of the two institutions — the Telecom Regulatory Authority of India (TRAI) or the TC — needs to be complemented by a similar widening of the scope of the other. This, since all of the regulator’s recommendations need to be cleared by the Telecom Commission (TC).
Recently, the cabinet approved renaming the Telecom Commission to the Digital Communications Commission (DCC) while industry watchdog Trai became Digital Communications Regulatory Authority of India. “These cannot be just name changes. One needs to keep in mind that this will be the policy of the government, not of any ministry. Some changes need to be made in the remit of the Digital Commission and the Trai Act as well. It’s a work in progress,” said another senior official of the telecom ministry. Currently, the TC—an inter-ministerial body, which is the highest decision-making authority of the DoT—is headed by the telecom secretary.
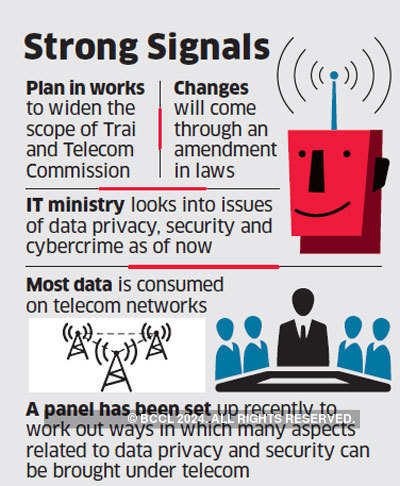
The full-time members of the commission are member (finance), member (production), member (services) and member (technology). Part-time members of the TC are CEO of Niti Aayog, secretary (Department of Economic Affairs), secretary, ministry of electronics and information technology (MeitY) and secretary (Department of Industrial Policy & Promotion). The TC was set up via a government resolution in 1989. Trai, on the other hand, is governed by the Trai Act of 1997.
An inter-ministerial team was formed three months ago which is working on ways in which many aspects related to data privacy and data security are moved under telecom, said another DoT official. The official added that the team of experts includes officials of MeitY and the ministry of information and broadcasting (I&B).
“We have instructions from the top officials in the government to see how all privacy and datarelated issues can be seamlessly looked into under the governance of TC,” the official said.
A senior Trai official also confirmed that meetings are on and this would also lead to additional responsibility for the sector regulator, which currently regulates all matters related just to the sector, with consumer interests at the heart of its actions. “The jurisdiction of TC will increase keeping cybercrime in mind. It is still in the planning stage but talks are on to ensure that all the work that is done by DoT in dealing with data safety is put forward,” said another official aware of the developments.
The government plans to table the draft personal data protection bill submitted by Justice BN Srikrishna Committee in Parliament by December after holding consultations with different ministries, industry representatives and the public.
The bill, submitted to the IT ministry, recommends a layered consent architecture and bringing in key principles of personal data processing, whereby companies should collect only the required data from an individual, state the purpose of its use explicitly, and store it only for as long as it is required.
As per the draft bill, citizens and internet users will have the final say on how and for what purpose personal data can be used, and they will also have the right to withdraw consent.
The Trai, on its own, in mid-July had released its recommendations on the subject titled ‘Privacy, Security and Ownership of Data in the Telecom Sector’, which are applicable for apps, browsers, operating systems and handset makers.
-GoITWay
According to officials in the Department of Telecommunications and the Telecom Regulatory Authority of India (Trai), these changes, which will come through an amendment in laws, underline the fact that consumers access most of their data via mobile phones, and hence the telecom department will need to get involved.
“We have to realise that subjects such as data privacy and security all flow through the telecom network. In fact, 93% of all such data is consumed on telecom networks, for example ecommerce, etc,” said a senior government official, who did not want to be named.
“Aspects of data privacy etc should all come under one ambit, and that should be the Digital Commission and the Digital Communications Regulator,” the official said.
Any change in the regulatory ambit of one of the two institutions — the Telecom Regulatory Authority of India (TRAI) or the TC — needs to be complemented by a similar widening of the scope of the other. This, since all of the regulator’s recommendations need to be cleared by the Telecom Commission (TC).
Recently, the cabinet approved renaming the Telecom Commission to the Digital Communications Commission (DCC) while industry watchdog Trai became Digital Communications Regulatory Authority of India. “These cannot be just name changes. One needs to keep in mind that this will be the policy of the government, not of any ministry. Some changes need to be made in the remit of the Digital Commission and the Trai Act as well. It’s a work in progress,” said another senior official of the telecom ministry. Currently, the TC—an inter-ministerial body, which is the highest decision-making authority of the DoT—is headed by the telecom secretary.

The full-time members of the commission are member (finance), member (production), member (services) and member (technology). Part-time members of the TC are CEO of Niti Aayog, secretary (Department of Economic Affairs), secretary, ministry of electronics and information technology (MeitY) and secretary (Department of Industrial Policy & Promotion). The TC was set up via a government resolution in 1989. Trai, on the other hand, is governed by the Trai Act of 1997.
An inter-ministerial team was formed three months ago which is working on ways in which many aspects related to data privacy and data security are moved under telecom, said another DoT official. The official added that the team of experts includes officials of MeitY and the ministry of information and broadcasting (I&B).
“We have instructions from the top officials in the government to see how all privacy and datarelated issues can be seamlessly looked into under the governance of TC,” the official said.
A senior Trai official also confirmed that meetings are on and this would also lead to additional responsibility for the sector regulator, which currently regulates all matters related just to the sector, with consumer interests at the heart of its actions. “The jurisdiction of TC will increase keeping cybercrime in mind. It is still in the planning stage but talks are on to ensure that all the work that is done by DoT in dealing with data safety is put forward,” said another official aware of the developments.
The government plans to table the draft personal data protection bill submitted by Justice BN Srikrishna Committee in Parliament by December after holding consultations with different ministries, industry representatives and the public.
The bill, submitted to the IT ministry, recommends a layered consent architecture and bringing in key principles of personal data processing, whereby companies should collect only the required data from an individual, state the purpose of its use explicitly, and store it only for as long as it is required.
As per the draft bill, citizens and internet users will have the final say on how and for what purpose personal data can be used, and they will also have the right to withdraw consent.
The Trai, on its own, in mid-July had released its recommendations on the subject titled ‘Privacy, Security and Ownership of Data in the Telecom Sector’, which are applicable for apps, browsers, operating systems and handset makers.
-GoITWay
Saturday, 27 October 2018
Fake bank apps may have stolen data of thousands of customers: Report
Fake apps of SBI, ICICI, Axis Bank, Citi and other leading banks are available on Google Play, which may have stolen data of thousands of bank customers, claims a report by IT security firm Sophos Labs.
These fake android apps have logo of respective banks which makes it difficult for customers to differentiate between the fake and original apps, it said.
The report further said that the deceptive malware in these apps may have stolen thousands of customers' account and credit card details.
When contacted some of the banks mentioned in the report said they have not come across any such fake apps.
However, some banks have started inquiry and also informed the CERT-In -- the national nodal agency for responding to computer security incident.
The fake apps target total seven banks like SBI, ICICI, Axis, Indian Overseas, BoB, Yes Bank and Citi Bank, the report said.
Another lender Yes Bank said it has informed the bank's cyber fraud department about the matter.
However, the country's largest lender State Bank of India's response was awaited.
There were no immediate comments from ICICI Bank and Axis Bank.
According to the report, the apps lured victims to download and use them, either by masquerading as Internet apps or e-wallets, promising rewards, including cash back on purchases, free mobile data or interest free loans.
Some even claimed to be providing a too-good-to-be-true service, enabling users to withdraw cash from an ATM and have it delivered to their doorstep.
"Deceptive malware may have stolen thousands of Indian sub-continent bank customers account data or credit card numbers," said Pankaj Kohli, threat researcher, SophosLabs.
Fake apps are not new to Android and this sort of malware will continue to find its way into the android app store, it said.
"Some are blatant copies of real apps, while a few are much more dangerous as they seed malware and steal data from user accounts. Users should always use antivirus software, which provides malware protection and internet security to keep users protected and stop these fake apps from stealing data," it said.
These fake android apps have logo of respective banks which makes it difficult for customers to differentiate between the fake and original apps, it said.
The report further said that the deceptive malware in these apps may have stolen thousands of customers' account and credit card details.
When contacted some of the banks mentioned in the report said they have not come across any such fake apps.
However, some banks have started inquiry and also informed the CERT-In -- the national nodal agency for responding to computer security incident.
The fake apps target total seven banks like SBI, ICICI, Axis, Indian Overseas, BoB, Yes Bank and Citi Bank, the report said.
Another lender Yes Bank said it has informed the bank's cyber fraud department about the matter.
However, the country's largest lender State Bank of India's response was awaited.
There were no immediate comments from ICICI Bank and Axis Bank.
According to the report, the apps lured victims to download and use them, either by masquerading as Internet apps or e-wallets, promising rewards, including cash back on purchases, free mobile data or interest free loans.
Some even claimed to be providing a too-good-to-be-true service, enabling users to withdraw cash from an ATM and have it delivered to their doorstep.
"Deceptive malware may have stolen thousands of Indian sub-continent bank customers account data or credit card numbers," said Pankaj Kohli, threat researcher, SophosLabs.
Fake apps are not new to Android and this sort of malware will continue to find its way into the android app store, it said.
"Some are blatant copies of real apps, while a few are much more dangerous as they seed malware and steal data from user accounts. Users should always use antivirus software, which provides malware protection and internet security to keep users protected and stop these fake apps from stealing data," it said.
Friday, 26 October 2018
AI will cause role changes, not necessarily job losses: Studies
More than half of generic work profiles are facing the risk of disruption over the next two years due to automation, according to an estimate by Teamlease Services.
However, this does not necessarily imply job losses as automation would throw up new job profiles for those getting substituted, experts said.
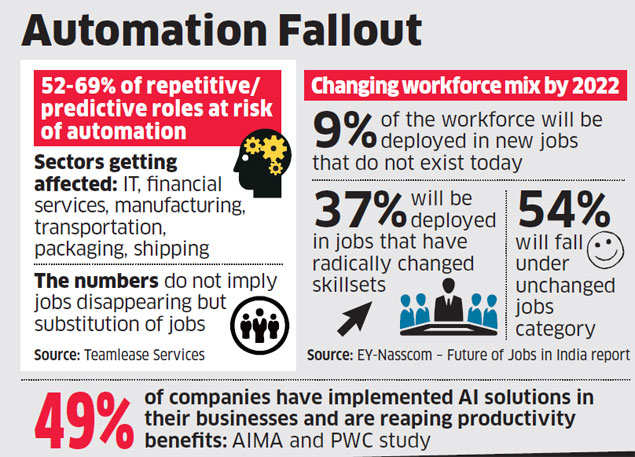
A Teamlease Services study, based on data from secondary sources, estimates 52-69% of repetitive and predictive roles in sectors including IT, financial services, manufacturing, transportation, packaging and shipping to get exposed to the risk of automation in the next couple of years.
“The data implies risk of automation. However, that does not mean it would lead to a job loss necessarily,” said Rituparna Chakraborty, co-founder of Teamlease Services, discrediting the oft-quoted premise that automation would lead to job loss.
“There’s a nuance that most people lose out on—jobs disappearing and substitution of jobs,” said Debabrat Mishra, partner at Deloitte. “This is not the first time we are witnessing the impact of technology and automation. For example, ATMs were supposed to do away with cashiers (at banks) but both coexist today. In fact, ATMs created more jobs in the backend in the form of call centres,” he explained.
Though employment-related concerns due to automation cannot be altogether ruled out, it would allow humans to get more involved in tasks that need higher specialisation and critical thinking, experts said.
As much as 49% companies that responded to a recent survey by the All India Management Association (AIMA) and PwC on how artificial intelligence is reshaping jobs said they had implemented AI solutions in their businesses and were reaping productivity benefits.
Roles getting rapidly disrupted include data-entry clerk, cashier, financial analyst, telemarketer, customer-service executive, manual work operator/executive, factory worker, computer support specialist, market research analyst, retail salesperson and advertising sales person.
However, several of the people getting replaced by automation will find higher-value-added jobs, said experts. Mishra qualified the substitution of jobs predicted as disruption. For instance, the role of a data-entry clerk will be taken over by machines but the role will be substituted by a data-validation clerk.
A cashier’s role would be substituted by a query handler, a financial analyst by an adviser, a telemarketer by a personal adviser or marketing algorithm builder, a customer service executive by a customer interaction executive and a retail salesperson by a retail adviser, style adviser or shopping assistant.
The AIMA survey stated that as AI systems continue to disrupt traditional industrial practices with their increasing prowess at tackling complex problems, they continue to raise employment-related concerns.
While 36% of decision-makers stated that overall, advancements in automation and technology had not displaced jobs, 46% said these would have a severe impact on employment in India. Further, nearly half the participants surveyed felt job automation was reasonably probable; however, it was likely to be partial, with humans retained for specific expertise.
“Based on the views of professionals working across different industrial sectors, we can conclude that most of the sectors are likely to be partially automated, but the chances of complete automation in the next five years are the highest in the manufacturing sector (38%), followed by the finance sector (31%),” the survey stated.
“There will be some impact on jobs in the short-term and jobs will not grow in massive numbers. However, in the next five years or so, the impact will even out as there will be new job creations and role substitutions,” said Pankaj Bansal, chief executive at PeopleStrong.
Salary levels will go up due to specialisation of skillsets and the acute dearth of talent qualified in new capabilities in India and the world over, he said.
According to a survey on the Future of Jobs in India by EY and Nasscom, there will be a change in workforce mix by 2022 due to increased adoption of technologies. By then, 9% of the workforce will be deployed in new jobs that do not exist today, 37% will be in jobs that have radically changed skillsets and 54% will fall under the unchanged jobs category.
Experts also stated that the impact of automation is no longer restricted to junior and middle level as creation of new categories of businesses is leading to senior-level jobs being redesigned with rapid adoption of AI, robotics, blockchain, etc. One recent instance of this was seen a couple of weeks ago, when Cognizant Technology Solutions let go of 200 employees at the senior level.
This was part of the company’s plan to align its talent pool to new digital requirements, replacing those who have not adopted to the new technology landscape with those with new skills.
“Organisations need the senior leadership positions to support these requirements—which could either happen through senior leadership upskill and leadership ability changes or hiring talent from outside,” said Anurag Malik, partner at EY.
The good news is that while technology is making inroads at a rapid pace and as new job profiles get created, there is an increasing demand for professionals trained in new skills who can help companies navigate through the transformation.
-GoITWay
However, this does not necessarily imply job losses as automation would throw up new job profiles for those getting substituted, experts said.
A Teamlease Services study, based on data from secondary sources, estimates 52-69% of repetitive and predictive roles in sectors including IT, financial services, manufacturing, transportation, packaging and shipping to get exposed to the risk of automation in the next couple of years.
“The data implies risk of automation. However, that does not mean it would lead to a job loss necessarily,” said Rituparna Chakraborty, co-founder of Teamlease Services, discrediting the oft-quoted premise that automation would lead to job loss.
“There’s a nuance that most people lose out on—jobs disappearing and substitution of jobs,” said Debabrat Mishra, partner at Deloitte. “This is not the first time we are witnessing the impact of technology and automation. For example, ATMs were supposed to do away with cashiers (at banks) but both coexist today. In fact, ATMs created more jobs in the backend in the form of call centres,” he explained.

Though employment-related concerns due to automation cannot be altogether ruled out, it would allow humans to get more involved in tasks that need higher specialisation and critical thinking, experts said.
As much as 49% companies that responded to a recent survey by the All India Management Association (AIMA) and PwC on how artificial intelligence is reshaping jobs said they had implemented AI solutions in their businesses and were reaping productivity benefits.
Roles getting rapidly disrupted include data-entry clerk, cashier, financial analyst, telemarketer, customer-service executive, manual work operator/executive, factory worker, computer support specialist, market research analyst, retail salesperson and advertising sales person.
However, several of the people getting replaced by automation will find higher-value-added jobs, said experts. Mishra qualified the substitution of jobs predicted as disruption. For instance, the role of a data-entry clerk will be taken over by machines but the role will be substituted by a data-validation clerk.
A cashier’s role would be substituted by a query handler, a financial analyst by an adviser, a telemarketer by a personal adviser or marketing algorithm builder, a customer service executive by a customer interaction executive and a retail salesperson by a retail adviser, style adviser or shopping assistant.
The AIMA survey stated that as AI systems continue to disrupt traditional industrial practices with their increasing prowess at tackling complex problems, they continue to raise employment-related concerns.
While 36% of decision-makers stated that overall, advancements in automation and technology had not displaced jobs, 46% said these would have a severe impact on employment in India. Further, nearly half the participants surveyed felt job automation was reasonably probable; however, it was likely to be partial, with humans retained for specific expertise.
“Based on the views of professionals working across different industrial sectors, we can conclude that most of the sectors are likely to be partially automated, but the chances of complete automation in the next five years are the highest in the manufacturing sector (38%), followed by the finance sector (31%),” the survey stated.
“There will be some impact on jobs in the short-term and jobs will not grow in massive numbers. However, in the next five years or so, the impact will even out as there will be new job creations and role substitutions,” said Pankaj Bansal, chief executive at PeopleStrong.
Salary levels will go up due to specialisation of skillsets and the acute dearth of talent qualified in new capabilities in India and the world over, he said.
According to a survey on the Future of Jobs in India by EY and Nasscom, there will be a change in workforce mix by 2022 due to increased adoption of technologies. By then, 9% of the workforce will be deployed in new jobs that do not exist today, 37% will be in jobs that have radically changed skillsets and 54% will fall under the unchanged jobs category.
Experts also stated that the impact of automation is no longer restricted to junior and middle level as creation of new categories of businesses is leading to senior-level jobs being redesigned with rapid adoption of AI, robotics, blockchain, etc. One recent instance of this was seen a couple of weeks ago, when Cognizant Technology Solutions let go of 200 employees at the senior level.
This was part of the company’s plan to align its talent pool to new digital requirements, replacing those who have not adopted to the new technology landscape with those with new skills.
“Organisations need the senior leadership positions to support these requirements—which could either happen through senior leadership upskill and leadership ability changes or hiring talent from outside,” said Anurag Malik, partner at EY.
The good news is that while technology is making inroads at a rapid pace and as new job profiles get created, there is an increasing demand for professionals trained in new skills who can help companies navigate through the transformation.
-GoITWay
Wednesday, 24 October 2018
Hackers have found a new way to sneak into computers and it’s through our own body heat.
Researchers at University of California found a new way of hacking, which is through a person’s own heat left by their fingers. When someone types in a password on their keyboards, they leave heat traces behind that are later picked up by hackers.
Naming the technique ‘Thermanator’, the team discovered this by using a thermal imaging camera and scanning the computer keyboard after a password has been typed. They noticed that key presses can be recovered as late as 30 seconds after the first key was pressed, reported Digital Trends.
Publishing their findings in a paper Thermanator, the researchers wrote, “Although thermal residue dissipates over time, there is always a certain time window during which thermal energy readings can be harvested from input devices to recover recently entered, and potentially sensitive, information.”
This style was tested by 31 participants on four keyboards and full passwords can be gained by scanning thermal residues on keyboards after 30 seconds. After a minute passed by, partial passwords were obtained. For the tests, the infrared heat-detecting FLIR cameras were set on tripod 24-inches away from the keyboard.
Thirty non-expert users were made to guess the password based on the scans. The participants were able to guess passwords between 19.5 and 31 seconds after the first presses. Weak passwords were guessed in an average of 25.5 seconds whereas passwords like ‘12341234’ took 45.25 seconds to guess.
“The main takeaway of this work is three-fold. First is using external keyboards to enter (already much-maligned) passwords is even less secure than previously recognized, second is to post factum (planned or impromptu) thermal imaging attacks are realistic, and finally perhaps it is time to either stop using keyboards for password entry, or abandon passwords altogether,” researchers said.
Researchers said that this type of attack could be used to gain access to text, banking pins, and/or codes. They hope that their findings will encourage a move towards more secure methods, wrote Mirror.
GoITWay
Tuesday, 23 October 2018
Facebook logs in, Bengaluru now hosts all big five tech firms
Facebook is taking up 2.2 lakh sqft office space in Bengaluru as the world’s largest social network is logging into the country’s technology capital, people familiar with the matter said.
It has taken up the space in Embassy Golf Links, an office parkthat houses marquee clients IBM, Microsoft, Goldman Sachs and reinsurer Swiss Re, among others.
The city’s booming commercial market will now house all the Big Five tech firms — Facebook, Amazon, Apple, Microsoft and Google — or FAAMG, an acronym coined by Wall Street investors.
Sources told TOI that Facebook is expected to move into the new facility next year and will employ 2,200 people. The exact nature of operations is not clear immediately. The social network giant will pay a rent of Rs 130 per sqft, or Rs 34 crore a year, sources added. An email sent to Facebook didn’t elicit a response. Embassy Office Parks declined comment.
It has taken up the space in Embassy Golf Links, an office parkthat houses marquee clients IBM, Microsoft, Goldman Sachs and reinsurer Swiss Re, among others.
The city’s booming commercial market will now house all the Big Five tech firms — Facebook, Amazon, Apple, Microsoft and Google — or FAAMG, an acronym coined by Wall Street investors.
Sources told TOI that Facebook is expected to move into the new facility next year and will employ 2,200 people. The exact nature of operations is not clear immediately. The social network giant will pay a rent of Rs 130 per sqft, or Rs 34 crore a year, sources added. An email sent to Facebook didn’t elicit a response. Embassy Office Parks declined comment.
Monday, 22 October 2018
All about India's data localisation policy
Several laws and regulators are converging on the hotbutton topic of data localisation. The deadline for a Reserve Bank of India (RBI) mandate for fintech firms to house data only in India lapsed last week. Other norms around holding accounting data dating back to 2014 locally, the draft ecommerce law that requires firms to locally store “community data collected by Internet of Things devices in public space” and “data generated by users in India from various sources including e-commerceplatforms, social media, search engines, etc,” only queer the pitch further.
What’s At Stake
There’s a massive explosion in data being generated by connected internet users in India. According to a report by real estate and infrastructure consultancy Cushman and Wakefield, the size of the digital population in India presents a huge potential demand for data centre infrastructure.
Digital data in India was around 40,000 petabytes in 2010; it is likely to shoot up to 2.3 million petabytes by 2020 — twice as fast as the global rate. If India houses all this data, it will become the second-largest investor in the data centre market and the fifth-largest data centre market by 2050, the consultancy has forecast.
Reactions Of Companies
Large tech companies are unhappy with such restrictive laws. Google’s privacy chief Keith Enright said in a recent blog post: “Mechanisms allowing for cross-border data flows are critical to the modern economy. Countries should adopt an integrated framework of privacy regulations, avoiding overlapping or inconsistent rules whenever possible.”
Indian Firms, Especially Startups, Are For It
Their push is from a data security angle and to safeguard India’s homegrown ventures. Companies such as Paytm and Phonepe have strongly endorsed data localisation, with a blog post from the latter contending that this move would “allow for better regulatory oversight and plug businessjurisdiction related loopholes that some foreign companies have long exploited to evade paying fair taxes in India.”
Issues Remain
Companies want to store, process and analyse data from multiple geographies. Some companies and lawyers argue that restricting the free flow of data may be counterproductive. “Excluding all Indian payment data from transfers is onerous, expensive, and can potentially limit the functionality which is currently available,” says Arun Prabhu, partner, Cyril Amarchand Mangaldas.
Now, A Trade Issue
While the tussle over data localisation started off within India, intense lobbying by tech MNCs has meant that this issue has now snowballed into one relating to free trade. Dennis Shea, the US ambassador to the WTO, has called for the banning of data localisation, even as US Senators John Cornyn and Mark Warner have called for India to soften its stance on the subject, according to a Reuters report.
Does Location Matter?
Technology experts such as Prashant Pradhan, vice-president and CTO (Asia Pacific) of IBM, argues that the physical location of data is irrelevant. Your data can be accessed from a server in Bengaluru or Boston just as easily. In fact, having a mirror of your data in India may actually increase the cost of operation and compliance. What’s more important is the quality, rather than sheer quantity. While terms such as big data were in vogue previously, what companies may be more interested in now is the quality of data they can secure and store. “While the amount of data itself has grown, what isn’t well understood is who has access to this data and what they can do with it,” he says.
Regulations Around The World
The European Union's General Data Protection Regulation doesn't have a specific data regulation rule, only stressing that cross-border data movement can happen if the other country has stringent rules to secure information. Several other countries have operationalised had various shades of data localisation.
Nigeria has, for example, required all subscriber and consumer data of tech and telecom firms and government data to be located locally, since 2013. Germany mandates that telecom and internet service providers store data locally, while Russia¡¦s rules mandate citizen data be stored within its borders.
However, by far, the most comprehensive laws are in China, where regulation covers not just personal information, but what is termed ¡§critical information infrastructure¡¨ that encompasses all aspects of daily life. Legal experts also say that the broad terminology paves the way for overt government access to this data and to build a strong cyber sovereignty.
Saturday, 20 October 2018
H-1B visa tweak may hurt IT firms
The Donald Trump administration has proposed changes to the H-1B registration process, which could lead to more permits being given to those with US master’s degrees, impacting Indian IT firms that rely on the work visa to service clients in that market.
The US General Services Administration said in a note that it was looking at a modified selection process in tune with the ‘Buy American and Hire American’ policies of the US government in a rule that was first proposed in 2011 to improve the intake and selection process of H-1B petitions. The US Citizenship and Immigration Services (USCIS) is the agency mandated to issue visas to immigrants.
“This regulation…would increase the probability of the total number of petitions selected under the cap filed for H-1B beneficiaries who possess a master’s or higher degree from a US institution of higher education each fiscal year,” it said. The US offers 65,000 standard H-1B visas for skilled workers and an additional 20,000 visas for workers with a US master’s degree or higher.
Typically, the agency processes the master’s pool and then sends petitions that are left over to the general pool. “Under the proposed rule, USCIS would first put all applicants in the general 65,000-visa pool. If that cap were reached, any additional US advanced degree holders would be redirected to the 20,000-visa pool,” US political news site Politico reported, citing sources at the Department of Homeland Security. “The administration expects the change could lead to a 15% increase in H-1B visa holders with US advanced degrees.”
For Indian IT companies, which predominantly employ people with bachelor’s degrees, the move could reduce the number of visas that are available for those without the advanced degrees. Some companies are already facing margin challenges as a result of tighter visa rules that require them to hire US citizens and sub-contract work when they cannot hire quickly enough.
“Increase in our sub-contractorcost, on-site localisation and investment impacted the margins by 50 basis points,” Infosys told analysts after its second-quarter results. The company’s margin was flat even as the rupee weakened significantly, which generally results in higher margins.
The company said it expects its sub-contractor costs to remain elevated, until it could staff projects with its own employees. Last year, Infosys said it would hire 10,000 American workers by 2020.
Despite the issue of tighter visas, IT CEOs do not believe the Indian talent model will fade away soon. “The fact is that the sheer demand for talent and the supply for talent is going to be met from places like India because demand far outstrips supply in those markets. But we have to be cognisant of the politics of it, so we need to be broad-based,” TCS CEO Rajesh Gopinathan said in an interview last week. “But I don’t think the demand for Indian talent is going to be outdated anytime soon.”
The US has issued over 19.07million of the 34.7 million H-1B visas issued in the decade to 2017 to applicants with post-graduation qualifications, the USCIS disclosed on its site. It did not, however, disclose whether the applicants had advanced degrees from US universities.
During the same period, those with bachelor’s degrees got 15.43 million work permits. The Trump administration is also looking to terminate by end of this year an Obama administration plan that allowed spouses of H-1B visa holders to work in the US.
The National Association of Software and Services Companies (Nasscom) said the Trump administration had said last year that it would begin making these changes to the programme and that the industry lobby would only be able to comment once an actual change was made. “We have always maintained that changing regulatory issues relating to the employer-employee provision, or the wages would simply increase the costs to the US companies that use the services of the industry to innovate and grow,” said Nasscom vice-president Shivendra Singh.
The US General Services Administration said in a note that it was looking at a modified selection process in tune with the ‘Buy American and Hire American’ policies of the US government in a rule that was first proposed in 2011 to improve the intake and selection process of H-1B petitions. The US Citizenship and Immigration Services (USCIS) is the agency mandated to issue visas to immigrants.
“This regulation…would increase the probability of the total number of petitions selected under the cap filed for H-1B beneficiaries who possess a master’s or higher degree from a US institution of higher education each fiscal year,” it said. The US offers 65,000 standard H-1B visas for skilled workers and an additional 20,000 visas for workers with a US master’s degree or higher.
Typically, the agency processes the master’s pool and then sends petitions that are left over to the general pool. “Under the proposed rule, USCIS would first put all applicants in the general 65,000-visa pool. If that cap were reached, any additional US advanced degree holders would be redirected to the 20,000-visa pool,” US political news site Politico reported, citing sources at the Department of Homeland Security. “The administration expects the change could lead to a 15% increase in H-1B visa holders with US advanced degrees.”
For Indian IT companies, which predominantly employ people with bachelor’s degrees, the move could reduce the number of visas that are available for those without the advanced degrees. Some companies are already facing margin challenges as a result of tighter visa rules that require them to hire US citizens and sub-contract work when they cannot hire quickly enough.
“Increase in our sub-contractorcost, on-site localisation and investment impacted the margins by 50 basis points,” Infosys told analysts after its second-quarter results. The company’s margin was flat even as the rupee weakened significantly, which generally results in higher margins.
The company said it expects its sub-contractor costs to remain elevated, until it could staff projects with its own employees. Last year, Infosys said it would hire 10,000 American workers by 2020.
Despite the issue of tighter visas, IT CEOs do not believe the Indian talent model will fade away soon. “The fact is that the sheer demand for talent and the supply for talent is going to be met from places like India because demand far outstrips supply in those markets. But we have to be cognisant of the politics of it, so we need to be broad-based,” TCS CEO Rajesh Gopinathan said in an interview last week. “But I don’t think the demand for Indian talent is going to be outdated anytime soon.”
The US has issued over 19.07million of the 34.7 million H-1B visas issued in the decade to 2017 to applicants with post-graduation qualifications, the USCIS disclosed on its site. It did not, however, disclose whether the applicants had advanced degrees from US universities.
During the same period, those with bachelor’s degrees got 15.43 million work permits. The Trump administration is also looking to terminate by end of this year an Obama administration plan that allowed spouses of H-1B visa holders to work in the US.
The National Association of Software and Services Companies (Nasscom) said the Trump administration had said last year that it would begin making these changes to the programme and that the industry lobby would only be able to comment once an actual change was made. “We have always maintained that changing regulatory issues relating to the employer-employee provision, or the wages would simply increase the costs to the US companies that use the services of the industry to innovate and grow,” said Nasscom vice-president Shivendra Singh.
Thursday, 18 October 2018
RBI Wants to Enable Seamless Transfer Between Mobile Wallets Using UPI
The Reserve Bank of India on Tuesday laid out guidelines that would allow for seamless payments between different mobile wallets, in a move that could further boost the use of digital payments in the country.
Mobile wallets such as the one run by SoftBank and Alibaba-backed Paytm have become popular in India after a ban on high-value currency in late 2016 pushed people to pay digitally. Mobile wallets currently do not allow users to send or receive money from a wallet run by another firm.
Digital wallet companies, if they so desire, can now use a state-backed payments network UPI that makes peer-to-peer payments instant, to make wallets inter-operable, the Reserve Bank of India said on Tuesday.
"It's going to increase the growth rate of digital payments in India even faster and, of course, create more business opportunities," said Upasna Taku, co-Founder of fintech firm MobiKwik, which operates a wallet.
Digital payments in India are projected to grow five-fold to about $1 trillion (roughly Rs. 72 lakh crores) by 2023, according to Credit Suisse.
Huawei has unveiled an AI strategy and a portfolio of supporting products built on two new microchips, which the telecoms giant claims is the world’s first AI IP and chip series designed for a full range of deployment scenarios.
The Ascend 310 is designed for the low-power computing needs of smart devices and the Ascend 910 for cloud computing. Huawei’s rotating chairman Eric Xu said the Ascend 910 has “greatest computing density in a single chip,” but denied that it was designed to provide direct competition for the likes of Qualcomm and Nvidia.
Huawei’s full-stack portfolio of AI products and cloud services. These are designed to adapt to public clouds, private clouds, edge computing, industrial IoT devices, consumer devices, and any other deployments, providing optimal efficiency for any scenario, whether the priority is minimising energy consumption or maximising computing power.
“‘Full stack means that Huawei is able to provide AI application developers with unparalleled computing power and a strong application development platform,”
Huawei’s AI strategy
Huawei has historically focused on building chips for its smartphones but is now developing them to power other enterprise applications.
Huawei’s AI strategy aims to increase adoption by offering faster model training, affordable computing power, AI deployment and user privacy, new algorithms, AI automation, practical applications, a real-time, closed-loop system, multi-tech synergy, platform support and talent availability, according to the company.
The products that will support these objectives include the Ascend chips series, a chip operators library and development toolkit, a training and inference framework, and application enablement for devices, edge and cloud computing through full-pipeline services, hierarchical APIs and pre-integrated solutions.
In September 2017, Huawei released Huawei Cloud EI, an AI service platform for enterprises and governments. In April 2018, Huawei announced HiAI, its AI engine for smart devices. The company’s full-stack, all-scenario AI portfolio is designed to provide powerful support for Huawei Cloud EI and HiAI.
-GoITWay
Wednesday, 17 October 2018
What is inventory management? A system for streamlining operations
What is an inventory management system?
An inventory management system tracks purchases, keeps count of goods and supplies in stock, and reorders supplies when levels get low. More sophisticated inventory management systems can track stock location and will even predict the optimum time to reorder supplies, drawing on a variety of data, including past sales and weather forecasts.
Inventory management systems integrate with — or may potentially replace — purchasing and sales systems, and they provide tools to reconcile stock levels calculated from purchasing and sales with real-world counts taken from warehouses via barcode scanners or RFID readers.
There are small business inventory systems you can run on a single PC, bigger software suites that run on premises or in the cloud, and inventory management modules for enterprise resource planning (ERP) systems.
Inventory management vs. ERP
In tracking inventory, an inventory management system provides a subset of the functionality of an ERP system, which also takes orders from customers, bills them, places orders with suppliers, pays them, pays your staff, and reports on how your business is doing. As such, inventory management is just one of the modules in a typical ERP system. That module may be enough, depending on the size of your ERP vendor and how much they know about the market you’re in, or you may want to turn to a specialist inventory management software vendor.
The benefits of inventory management software
If your business buys and sells goods and materials, inventory management can provide an essential overview of your operations, beyond simply tracking what you’ve bought and what you’ve sold. A good inventory management system can benefit your business by ensuring that you never have to tell a customer you’re out of stock, which can hurt your sales and reputation. An inventory management system can also help minimize levels of raw materials, work in progress and finished goods, enabling your organization to avoid tying up capital in unnecessary stock and save on warehousing costs by renting just enough space and no more.
Tracking how long perishable — or fashionable — goods typically hang around in your warehouse can also save you money, enabling you to limit stocks to just what you can sell before they go out of date or out of style.
Plus, inventory management isn’t just a good idea, it’s the law: Disclosing total inventory is a financial reporting requirement in many jurisdictions.
How does inventory management software work?
At its simplest, inventory management software adds up stock as it comes in and subtracts what gets sold, stolen or discarded. To ensure you don’t run out of stock, or space to store it, the software will make forecasts about how quickly stock will go out the door, and how long it will take to get new stock in, based on past performance data, such as recent sales, seasonal sales performance, and how long it typically takes your suppliers to deliver.
More sophisticated systems can use additional factors — weather reports, store schedules, anything you can turn into a number — to fine-tune those forecasts.
Inventory management features
An inventory management system can offer a lot more functionality than simply counting your inventory, depending on how much you're willing to pay, where you're running it, and what other applications you're willing to integrate with it.
Scanning barcodes is almost a given these days, even at the corner store, allowing the software to automatically update stock levels from the point of sale. Processing RFID tags takes things to the next level, allowing you to track not just which product, but which instance of a product, has been shipped or sold.
The software may be able to generate reports on inventory variations or forecast seasonal demand, allowing you to order raw materials and plan production to maximize sales. It may also automate elements of your business, automatically reordering when stock levels run low — especially useful for irregularly selling items you don't pay much attention to — and generating purchase orders and invoices, perhaps by integrating with your accounting software.
If you take orders or prepare estimates for clients on site, you'll want remote access to your inventory so you can promise realistic delivery dates: A system with a tablet or smartphone interface is a must.
The ability to track inventory across multiple locations is important if your company has warehouses around the country or makes intra-company sales.
Finally, an inventory management system that can perform "kitting" will make it easier for you to track the whole bills of materials for a finished product, whether it's a car or just the deluxe widget kit (complete with widget, spare battery and cleaning cloth).
Inventory management offerings
It needn't cost the earth to start managing your inventory. If your needs are modest, then there are free cloud systems out there that can help.
Delivrd, for example, will manage up to 10 product lines at a single inventory location. Pay $49.99 per month to manage unlimited products at unlimited locations, or twice that to integrate it with your e-commerce or order-picking systems.
Also in the cloud, Zoho has added an inventory management module to its CRM and collaboration platform. It offers features such as kitting and automatic reordering for free, but if you want to process more than a handful of orders a week or get a centralized view of multiple warehouses, you'll have to pay anywhere from $29 per month (for 10 users and 100 online orders) to $249 per month (for unlimited users and 30,000 online orders).
There are open source systems too, typically modules within broader open source ERP systems such as OpenBravo, Apache's OFBiz, or Odoo. OpenBravo and Odoo charge for support services around their software; Apache leaves that to third parties.
Further up the scale, several major enterprise software vendors also offer inventory management for their platforms. For example, Oracle Inventory Management integrates with the company's purchasing, manufacturing and supply chain software, and is available in the cloud or on premises. SAP offers many inventory management functions in its sprawling ERP system, and with its move to the S/4HANA in-memory platform much of that inventory analysis can be performed in real time.
AI in inventory management
Predictably, artificial intelligence is being used to enhance predictions or check that inventory records match reality. It’s being used to spot trends in what sells when, identifying the perfect weather for barbecue, and to improve inspection of goods in, ensuring orders match deliveries.
For more on the use of AI in inventory management, see “How AI will revolutionize inventory management.”
Predictably, artificial intelligence is being used to enhance predictions or check that inventory records match reality. It’s being used to spot trends in what sells when, identifying the perfect weather for barbecue, and to improve inspection of goods in, ensuring orders match deliveries.
For more on the use of AI in inventory management, see “How AI will revolutionize inventory management.”
IoT in inventory management
Inventory management is fertile territory for the internet of things (IoT) to grow. Goods are now routinely tagged with RFID, allowing machines to track not only how much stock is on hand but where it is with ever-increasing precision. But the falling cost of sensors is making it easier to record not just where something is, but at what temperature it’s been stored and how hard it’s been dropped, at an increasingly granular level.
-GoITWay
Google may open eStore by November in India
Google is eyeing the e-commerce market in India. Except, it won’t be doing any direct commerce there.
Come November, Google plans to launch an online storefront for all its branded hardware products, ET has learnt. These would include its flagship smartphone Pixel, Chromecast, Google Home smart speakers, and virtual reality headset, Daydream.
The storefront, similar to Apple’s storefront for the India market, will be a website where Google will merely display its branded and licensed hardware products. But it will also be able to gain access to customer data and have a stronger influence over the buying experience.
“We are looking to launch a Google-branded online store for all hardware launched in India, with an authorised partner who will operate and manage the fulfilment,” a company spokesperson confirmed in an emailed statement.
Google, sources say, is in talks with several third-party partners for this, including Ingram Micro.
“A storefront allows Google to access info on the premium users looking to buy its phones. Second, it also helps the brand to control the end-to-end selling experience and have the ability to cross-sell other products and offerings, like bundling Google Home or accessories, or even, in the future, extended warranty plans or upgrade programs like Apple does well with Apple Care,” said Neil Shah, partner at Counterpoint Research.
In 2017, Google’s market share in India was 0.07% of the overall smartphone market, while in the premium category (smartphones above $600), it was 3%, according to market research company Counterpoint Research. In the first nine months of 2018, those numbers fell to 0.03% and 1.6%, respectively.
Google’s move comes at a time when other smartphone companies such as Samsung and Xiaomi have been coming up with their own ecommerce offerings. Manu Jain, the country head of Xiaomi, in an earlier interaction with ET had stastated that Mi.com, the company’s ecommerce website, had become “the third-largest (ecommerce website) in India” in terms of overall gross merchandise value (GMV), a proxy for gross sales.
Google’s pre-launch version of its India storefront (store.google.com) allows users to find both online and offline retailers where they could purchase its products from. That will change in November, with users getting an option to purchase, with a redirection to the partner’s page, upon which the transaction can be completed. This is unlike Google’s home market, the United States, where Google’s store is managed and fulfilled by the company.
Come November, Google plans to launch an online storefront for all its branded hardware products, ET has learnt. These would include its flagship smartphone Pixel, Chromecast, Google Home smart speakers, and virtual reality headset, Daydream.
The storefront, similar to Apple’s storefront for the India market, will be a website where Google will merely display its branded and licensed hardware products. But it will also be able to gain access to customer data and have a stronger influence over the buying experience.
“We are looking to launch a Google-branded online store for all hardware launched in India, with an authorised partner who will operate and manage the fulfilment,” a company spokesperson confirmed in an emailed statement.
Google, sources say, is in talks with several third-party partners for this, including Ingram Micro.
“A storefront allows Google to access info on the premium users looking to buy its phones. Second, it also helps the brand to control the end-to-end selling experience and have the ability to cross-sell other products and offerings, like bundling Google Home or accessories, or even, in the future, extended warranty plans or upgrade programs like Apple does well with Apple Care,” said Neil Shah, partner at Counterpoint Research.
In 2017, Google’s market share in India was 0.07% of the overall smartphone market, while in the premium category (smartphones above $600), it was 3%, according to market research company Counterpoint Research. In the first nine months of 2018, those numbers fell to 0.03% and 1.6%, respectively.
Google’s move comes at a time when other smartphone companies such as Samsung and Xiaomi have been coming up with their own ecommerce offerings. Manu Jain, the country head of Xiaomi, in an earlier interaction with ET had stastated that Mi.com, the company’s ecommerce website, had become “the third-largest (ecommerce website) in India” in terms of overall gross merchandise value (GMV), a proxy for gross sales.
Google’s pre-launch version of its India storefront (store.google.com) allows users to find both online and offline retailers where they could purchase its products from. That will change in November, with users getting an option to purchase, with a redirection to the partner’s page, upon which the transaction can be completed. This is unlike Google’s home market, the United States, where Google’s store is managed and fulfilled by the company.
-GoITWay
Dell acknowledges India's data concerns, expects ripple effect
Dell Technologies chief executive Michael Dell said he’s not surprised that India is insisting on data localisation given security and privacy concerns and expects other nations to take a similar approach.
“If you don't know where your data is or it’s gotten into the wrong hands, it can be a very, very dangerous problem,” he told ET in an interview in Mumbai. “I would not be surprised if pretty much every country in the world creates something like this.”
Information is more valuable than applications and problems will arise when data get leaked or compromised.
THUMBS UP TO DIGITISATION DRIVE
“Every business at the end of the day is based on some kind of trust or assurance,” Dell said. “With greater connectivity, artificial intelligence, machine learning and deep learning neural networks in play, data can be used to create even better outcomes.”
The central bank has asked global payments companies such as Visa and MasterCard to ensure that transaction data of Indian customers is only stored locally. Most companies have either complied with this or submitted a schedule for doing so, ET reported on Monday, which was the deadline.
Dell said he was impressed by India’s digitisation drive, which was unique in terms of scale. “These (initiatives) are a platform for tremendous amount of growth and innovation and no other country in the world is doing this in any way close to what India is,” he said.
“The economic opportunities that come from inclusive growth will be tremendous. On top of this, a vibrant ecosystem of startups and individuals getting more opportunities will create a positive growth environment.”
Dell said the company’s India expansion exceeded those of many other territories. “The India business is growing at a faster clip than other major geographies,” he said. “But we can do more, we have this saying inside Dell which goes — PBNS, pleased but never satisfied.”
“If you don't know where your data is or it’s gotten into the wrong hands, it can be a very, very dangerous problem,” he told ET in an interview in Mumbai. “I would not be surprised if pretty much every country in the world creates something like this.”
Information is more valuable than applications and problems will arise when data get leaked or compromised.
THUMBS UP TO DIGITISATION DRIVE
“Every business at the end of the day is based on some kind of trust or assurance,” Dell said. “With greater connectivity, artificial intelligence, machine learning and deep learning neural networks in play, data can be used to create even better outcomes.”
The central bank has asked global payments companies such as Visa and MasterCard to ensure that transaction data of Indian customers is only stored locally. Most companies have either complied with this or submitted a schedule for doing so, ET reported on Monday, which was the deadline.
Dell said he was impressed by India’s digitisation drive, which was unique in terms of scale. “These (initiatives) are a platform for tremendous amount of growth and innovation and no other country in the world is doing this in any way close to what India is,” he said.
“The economic opportunities that come from inclusive growth will be tremendous. On top of this, a vibrant ecosystem of startups and individuals getting more opportunities will create a positive growth environment.”
Dell said the company’s India expansion exceeded those of many other territories. “The India business is growing at a faster clip than other major geographies,” he said. “But we can do more, we have this saying inside Dell which goes — PBNS, pleased but never satisfied.”
Tuesday, 16 October 2018
AI tool can help develop apps that drain less battery
WASHINGTON: Scientists, including one of Indian origin, have created an artificial inteligence (AI) tool to help developers design smartphone apps that drain less battery. "DiffProf" -- the tool designed by researchers at Purdue University in the US -- automatically decides for the developer whether an app feature has room for improving energy efficiency.
Scientists, including one of Indian origin, have created an artificial inteligence (AI) tool to help developers design smartphone apps that drain less battery. "DiffProf" -- the tool designed by researchers at Purdue University in the US -- automatically decides for the developer whether an app feature has room for improving energy efficiency.
How a code runs can dramatically differ between two apps, even if the developers are implementing the same task.
DiffProf catches these differences in the "call trees" of similar tasks, to show why the messaging feature of one app consumes more energy than another. DiffProf then reveals how to rewrite the app to drain less battery.
"Ultimately, in order for this technique to make a big difference for an entire smartphone, all developers would need to make their apps more energy-efficient," said Abhilash Jindal, a former PhD student at Purdue.
"The impact also depends on how intensively someone uses certain apps. Someone who uses messaging apps a lot might experience longer battery life, but someone who doesn't use their messaging apps at all might not," he said.
So far, the DiffProf prototype has only been tested for the Android mobile operating system, researchers said. MHN
-GoITWay
 Scientists, including one of Indian origin, have created an artificial inteligence (AI) tool to help developers design smartphone apps that drain less battery. "DiffProf" -- the tool designed by researchers at Purdue University in the US -- automatically decides for the developer whether an app feature has room for improving energy efficiency.
Scientists, including one of Indian origin, have created an artificial inteligence (AI) tool to help developers design smartphone apps that drain less battery. "DiffProf" -- the tool designed by researchers at Purdue University in the US -- automatically decides for the developer whether an app feature has room for improving energy efficiency. How a code runs can dramatically differ between two apps, even if the developers are implementing the same task.
DiffProf catches these differences in the "call trees" of similar tasks, to show why the messaging feature of one app consumes more energy than another. DiffProf then reveals how to rewrite the app to drain less battery.
"Ultimately, in order for this technique to make a big difference for an entire smartphone, all developers would need to make their apps more energy-efficient," said Abhilash Jindal, a former PhD student at Purdue.
"The impact also depends on how intensively someone uses certain apps. Someone who uses messaging apps a lot might experience longer battery life, but someone who doesn't use their messaging apps at all might not," he said.
So far, the DiffProf prototype has only been tested for the Android mobile operating system, researchers said. MHN
-GoITWay
Monday, 15 October 2018
Job fraud cases : Cyber Crime police ask web portals to carry disclaimers
A spurt in job frauds has led cybercrime police to request job portals to carry a disclaimer, warning people about frauds on their homepage.
"Fraudsters extract contact details of jobseekers from portals. They ‘offer’ jobs to people, claiming to be from MNCs. Now the portals display a disclaimer at the bottom of their homepage, warning people about such frauds," said Raghu Vir, additional DCP, cybercrime, Hyderabad.
Every month, at least five cases of job frauds get registered and cops have managed to solve nearly 50% of them.
"Most offenders have been traced to Delhi, Noida and some from Bangalore. Several Nigerians, too, are involved. These fraudsters rent a small place and hire a few people who go through the job portals. Later they send fake emails to see how many responses they get," said S Harinath, ACP, cybercrime, Rachakonda. "Youngsters are approaching us on Facebook to verify authenticity of companies that offer them jobs. We give them suggestions," said DCP Raghu Vir.
"Fraudsters extract contact details of jobseekers from portals. They ‘offer’ jobs to people, claiming to be from MNCs. Now the portals display a disclaimer at the bottom of their homepage, warning people about such frauds," said Raghu Vir, additional DCP, cybercrime, Hyderabad.
Every month, at least five cases of job frauds get registered and cops have managed to solve nearly 50% of them.
"Most offenders have been traced to Delhi, Noida and some from Bangalore. Several Nigerians, too, are involved. These fraudsters rent a small place and hire a few people who go through the job portals. Later they send fake emails to see how many responses they get," said S Harinath, ACP, cybercrime, Rachakonda. "Youngsters are approaching us on Facebook to verify authenticity of companies that offer them jobs. We give them suggestions," said DCP Raghu Vir.
No internet shutdown in India: Cyber Security official
NEW DELHI: A top government cybersecurity official on Friday clarified that India will not face any internet shutdown, quashing fears of an internet blackout in the country amid reports of a global outage. Russia Today had earlier reported that internet users across the globe may experience widespread network failures due to routine maintenance of key domain servers over the next 48 hours.
Speaking to NDTV, National Cyber Security Coordinator, Gulshan Rai, said, "All arrangements are in place and there will be no internet shutdown in India as is being circulated in the media."
The Russia Today report stated that the Internet Corporation of Assigned Names and Numbers (ICANN will carry out maintenance work during the 48 hours by changing the cryptographic key that helps protect the internet's address book or the Domain Name System (DNS).
This has been necessitated to counter the rising incidents of cyber attacks, Russia Today cited ICANN as saying. However, ICANN later clarified that the report had a "clickbait" headline and that the impact on users would be minimal.
"Unfortunately, that story carries a headline that is a click bait. There will be minimal impact to users. Note that data analysis suggests that more than 99% of users whose resolvers are validating will be unaffected," an ICANN spokesperson told NDTV.
The spokesperson further stated that "It has been about 20 hours since the rollover and based on all information we have, everything is going smoothly. There have been only a small handful of reports of issues suspected to be caused by the rollover. In all cases, it appears the impact was minor and the issues were quickly resolved."
Monday, 8 October 2018
What is a data artist? A role for drawing IT and business together
Charles Joseph Minard is arguably the world’s most famous data artist. By combining several data sets, including troop numbers, direction, temperature and terrain, he created in 1869 a visualization of Napoleon’s 1812 Russian campaign. Though that military exercise ended in disaster, Minard’s map remains “one of the best statistical drawings ever created.”
Were he alive today, perhaps Minard would find success in the emerging role of data artist, thanks to the incredible volume and availability of data and the speed and processing power of modern technology. Today’s data artists bridge the gap between IT and business, creating visualizations from terabytes of obscure data that can quickly and easily be viewed and understood by business leaders to help accelerate decision-making and improve the odds of success.
Data artist role and responsibilities
With today’s emphasis on data-driven decision-making, the data artist role is quickly becoming critical, says Justin Langseth, CEO and founder of Zoomdata. While the rise of the data scientist has been a major step forward in helping organizations make sense of their data, a chasm of understanding remains between the technical data analysts and business professionals. That gap has necessitated a new role that combines the technical expertise of a data scientist with the creative abilities of artists and graphic designers, Langseth says.
“In the midst of all the conversations around AI, big data, machine learning, data-driven decision-making, we realized that more enterprises were trying to tell stories based on their data using infographics, but that wasn’t telling the whole story,” Langseth says. “The problem is that infographics are static — information is constantly streaming in and new data can mean new results. There’s also a comprehension gap — businesspeople not understanding the same ‘language’ that technical data scientists are speaking. So, a data artist bridges that gap by presenting the technical information in ways that are easy to understand, through visualizations.”
The benefits of hiring data artists
Data artists can help provide competitive advantage by improving an organization’s ability to make beneficial decisions fast. Because data artists also possess the skills to make data visualizations interactive, businesspeople and IT leaders can perform “what-if” analysis and/or slice and dice data sets to home in on specific areas of importance, Langseth says. That means businesses can make better decisions faster — a key to keeping ahead of the competition, he adds.
“In IT, everyone has pretty much the same access to the best CRM system or whatever technologies are available,” Langseth says. “You’re not going to out-innovate competitively because of that tech alone, though. It’s what you’re able to do with that technology that matters. It’s going to be the companies who can make better decisions, faster, based on better data, that they can quickly and easily understand. With real-time analysis provided by data artists, you can experiment with different options and see different outcomes, and then figure out how to optimize your business for better results.”
For Charles Boicey, co-founder and chief innovation officer at cloud-based healthcare data visualization platform Clearsense, data artists help support better financial, operational and business — even clinical — outcomes.
“This is two-fold, for us, as a company serving the healthcare market. For IT and the business, it’s incredibly important, but also for clinicians, who have different needs when it comes to the data,” Boicey says. “If you can put patient data in a format where they can understand it at a glance, that can lead to better decision-making and better patient outcomes — which then circles back and leads to better business and financial outcomes, too.”
Data artist skills
Data artists have a unique combination of skills: part programmer, part data scientist and part visual artist, says Langseth. Data artists need computer science and programming skills to render data visually; data science skills to identify the relevant data and format it correctly; and visual design and creative skills to transform data into images that are easily digestible, he says.
“It’s such a hybrid position that requires all of these skills — JavaScript is one of the main languages used in this role, but also open source tools to help design custom visualizations. You also need to work closely with data scientists, so data literacy is key. And there’s even a bit of educational psychology involved, because you need to understand human beings’ visual processing abilities and how they understand information,” he says.
Were he alive today, perhaps Minard would find success in the emerging role of data artist, thanks to the incredible volume and availability of data and the speed and processing power of modern technology. Today’s data artists bridge the gap between IT and business, creating visualizations from terabytes of obscure data that can quickly and easily be viewed and understood by business leaders to help accelerate decision-making and improve the odds of success.
Data artist role and responsibilities
With today’s emphasis on data-driven decision-making, the data artist role is quickly becoming critical, says Justin Langseth, CEO and founder of Zoomdata. While the rise of the data scientist has been a major step forward in helping organizations make sense of their data, a chasm of understanding remains between the technical data analysts and business professionals. That gap has necessitated a new role that combines the technical expertise of a data scientist with the creative abilities of artists and graphic designers, Langseth says.
“In the midst of all the conversations around AI, big data, machine learning, data-driven decision-making, we realized that more enterprises were trying to tell stories based on their data using infographics, but that wasn’t telling the whole story,” Langseth says. “The problem is that infographics are static — information is constantly streaming in and new data can mean new results. There’s also a comprehension gap — businesspeople not understanding the same ‘language’ that technical data scientists are speaking. So, a data artist bridges that gap by presenting the technical information in ways that are easy to understand, through visualizations.”
The benefits of hiring data artists
Data artists can help provide competitive advantage by improving an organization’s ability to make beneficial decisions fast. Because data artists also possess the skills to make data visualizations interactive, businesspeople and IT leaders can perform “what-if” analysis and/or slice and dice data sets to home in on specific areas of importance, Langseth says. That means businesses can make better decisions faster — a key to keeping ahead of the competition, he adds.
“In IT, everyone has pretty much the same access to the best CRM system or whatever technologies are available,” Langseth says. “You’re not going to out-innovate competitively because of that tech alone, though. It’s what you’re able to do with that technology that matters. It’s going to be the companies who can make better decisions, faster, based on better data, that they can quickly and easily understand. With real-time analysis provided by data artists, you can experiment with different options and see different outcomes, and then figure out how to optimize your business for better results.”
For Charles Boicey, co-founder and chief innovation officer at cloud-based healthcare data visualization platform Clearsense, data artists help support better financial, operational and business — even clinical — outcomes.
“This is two-fold, for us, as a company serving the healthcare market. For IT and the business, it’s incredibly important, but also for clinicians, who have different needs when it comes to the data,” Boicey says. “If you can put patient data in a format where they can understand it at a glance, that can lead to better decision-making and better patient outcomes — which then circles back and leads to better business and financial outcomes, too.”
Data artist skills
Data artists have a unique combination of skills: part programmer, part data scientist and part visual artist, says Langseth. Data artists need computer science and programming skills to render data visually; data science skills to identify the relevant data and format it correctly; and visual design and creative skills to transform data into images that are easily digestible, he says.
“It’s such a hybrid position that requires all of these skills — JavaScript is one of the main languages used in this role, but also open source tools to help design custom visualizations. You also need to work closely with data scientists, so data literacy is key. And there’s even a bit of educational psychology involved, because you need to understand human beings’ visual processing abilities and how they understand information,” he says.
Friday, 5 October 2018
Five things to know about the Facebook hack
Facebook reported its worst security breach on 25 September, in which at least 50 million accounts were compromised and another 40 million were considered to be at risk by the social media network. Mint tells you what you need to know about the breach.
1. What has happened?
Facebook found three bugs in its video uploader, which would occasionally appear when using the “View As” feature. This is a feature that allows you to look at your Facebook Timeline as someone else. Hackers stole access tokens, giving them entry into your account. An access token is a code that identifies the user and allows other apps, browsers, etc., to access your information. This is how your browser keeps you logged in to Facebook despite closing the page. An access token does not store your password, so stealing it doesn’t give hackers your password. Access tokens are also generated by Gmail, Twitter and many other websites.
2. How will you know if you were affected?
Facebook logged 90 million of its users out of their accounts, as a result of resetting their access tokens. According to the company, 50 million users have been affected by the hack and an additional 40 million were logged out because they accessed the “View As” feature since the vulnerability entered Facebook’s code. If you were one of Facebook users affected by the breach, you would have seen a post at the top of your News Feed, notifying you of the breach. Since access tokens do not include passwords, you don’t have to change your Facebook password if you were affected.
3. Has the bug been fixed?
Facebook said the leak was plugged on 27 September, though it is continuing the probe into the matter. Access tokens for affected accounts were reset, but Facebook isn’t sure if personal information was accessed.

4. Are accounts other than Facebook affected?
Technically, yes. Having your access token would let attackers access all websites and apps that use your Facebook account for authentication. That includes food delivery and dating apps and many others. This is why users had to re-log in to those apps as well because the access tokens they had have now been invalidated. You can find information on apps that you have logged into using Facebook from the social network’s own settings. The “Apps and Websites” option will show you this.
5. How is this breach different from the Cambridge Analytica (CA) scandal?
The main difference between this breach and the CA scandal is that this one is an actual hack: there was a vulnerability in Facebook’s software. In the CA scandal, a researcher exploited Facebook’s data-sharing policies for his gain. Facebook hasn’t yet disclosed what information the hackers accessed. If personal information was leaked, Facebook may be punished under GDPR, as many of the affected users would have been from Europe.
1. What has happened?
Facebook found three bugs in its video uploader, which would occasionally appear when using the “View As” feature. This is a feature that allows you to look at your Facebook Timeline as someone else. Hackers stole access tokens, giving them entry into your account. An access token is a code that identifies the user and allows other apps, browsers, etc., to access your information. This is how your browser keeps you logged in to Facebook despite closing the page. An access token does not store your password, so stealing it doesn’t give hackers your password. Access tokens are also generated by Gmail, Twitter and many other websites.
2. How will you know if you were affected?
Facebook logged 90 million of its users out of their accounts, as a result of resetting their access tokens. According to the company, 50 million users have been affected by the hack and an additional 40 million were logged out because they accessed the “View As” feature since the vulnerability entered Facebook’s code. If you were one of Facebook users affected by the breach, you would have seen a post at the top of your News Feed, notifying you of the breach. Since access tokens do not include passwords, you don’t have to change your Facebook password if you were affected.
3. Has the bug been fixed?
Facebook said the leak was plugged on 27 September, though it is continuing the probe into the matter. Access tokens for affected accounts were reset, but Facebook isn’t sure if personal information was accessed.

4. Are accounts other than Facebook affected?
Technically, yes. Having your access token would let attackers access all websites and apps that use your Facebook account for authentication. That includes food delivery and dating apps and many others. This is why users had to re-log in to those apps as well because the access tokens they had have now been invalidated. You can find information on apps that you have logged into using Facebook from the social network’s own settings. The “Apps and Websites” option will show you this.
5. How is this breach different from the Cambridge Analytica (CA) scandal?
The main difference between this breach and the CA scandal is that this one is an actual hack: there was a vulnerability in Facebook’s software. In the CA scandal, a researcher exploited Facebook’s data-sharing policies for his gain. Facebook hasn’t yet disclosed what information the hackers accessed. If personal information was leaked, Facebook may be punished under GDPR, as many of the affected users would have been from Europe.
Friday, 28 September 2018
What's valid and what's not: Everything you need to know about today's Aadhaar verdict
The Supreme Court has upheld the Aadhaar scheme as constitutionally valid. However, the apex court's five-judge constitution bench also struck down several provisions in the Aadhaar Act.
Below are some of the highlights of the court verdict:
* The Supreme Court upheld the validity of Aadhaar saying sufficient security measures are taken to protect data and it is difficult to launch surveillance on citizens on the basis of Aadhaar. A five-judge bench led by CJI Dipak Misra asked the government to provide more security measures as well as reduce the period of storage of data.
* The SC asked the Centre to bring a robust law for data protection as soon as possible.
* The SC said Aadhaar cannot be made mandatory for openings of a bank account and for getting mobile connections.
* The SC said that Aadhaar must not be made compulsory for school admission and the administration cannot make it mandatory.
* The SC directed the government to ensure that illegal migrants are not issued Aadhaar to get benefits of social welfare schemes.
* Private companies can't ask for Aadhaar.
* Justice Sikri while reading out the verdict on the constitutional validity of Aadhaar said that there is a fundamental difference between Aadhaar card and identity. Once the bio-metric information is stored, it remains in the system, he said.
* The apex court struck down the provision in Aadhaar law allowing sharing of data on the ground of national security.
* The SC said there is a fundamental difference between Aadhaar and other identity proof as Aadhaar cannot be duplicated and it is a unique identification. It added that Aadhaar is to empower the marginalised sections of the society, and it gives them an identity.
* Aadhaar satisfies the doctrine of proportionality, said justice Sikri, adding, "It is better to be unique than to be best."
-GoITWay
Thursday, 27 September 2018
Every cyberattack is related to geopolitical conditions,' says CEO of cybersecurity company hired by Google
CNBC's Jim Cramer gets the latest on cybersecurity from FireEye CEO Kevin Mandia, whose company was hired by Google to defend against state-sponsored cyberattacks.
Mandia says that the "dead reality" is that every major cyberattack is somehow state-condoned.
In his more than 20 years responding to cyberbreaches, Kevin Mandia, the CEO of enterprise-facing cybersecurity company FireEye, has learned one key, overarching thing about cyberattacks.
"It took me too long, but here's the dead reality: every cyberattack's related to geopolitical conditions," he told CNBC on Tuesday in an interview with "Mad Money" host Jim Cramer.
"If you're in the United States and you hack a company, you're going to get caught, so you have to live in a safe harbor," Mandia said. "You almost have to be condoned, you have to be supported, and many of the attacks we respond to, there are, in fact, people in uniform conducting the attacks against our companies."
Mandia, whose company was hired by both Facebook and Google to help identify disinformation campaigns, said that while hackers still frequently target individuals, most hacks surveyed by FireEye in the last year had ties to foreign government entities.
"We responded to over 600 breaches last year," Mandia said. "I would say over 80 percent of them were state-sponsored or state-condoned, meaning the heads of the state or the heads of certain agencies of that state knew the attacks were ongoing, but there's no risk or repercussions to the attackers."
Mandia's statements come at a time when cyberattacks on both Wall Street and Main Street, with tech giants warning consumers about the billions of cyberattacks that happen every day and others fretting about how cyber-warfare could affect the 2018 midterm elections.
One of Mandia's top concerns was the lack of "segregation" between government, enterprise and individuals' networks, he said, cautioning that as the lines are blurred, hackers will likely go after more vulnerable targets and cause malware to "ripple" out through various systems.
"We're all blending together into this big mesh network and it could be the strategy of the adversaries to go after the softer targets," he warned. "If you hack every elementary school in a certain state, that means maybe employees aren't going to work that day, and then it ripples out from there."
And state-sponsored hacks from nations like Iran, with which U.S. representatives clashed at the United Nations General Assembly on Tuesday, are nowhere near quieting down, the FireEye chief said.
"We first responded to Iran in 2007, 2008, and they just looked like they had just gotten out of the classroom. They weren't very good in offensive cyber, but they've had 10 years now," he told Cramer.
"You know for a fact they had an agenda to get good at asymmetric warfare. Cyberattacks are, in fact, asymmetric," Mandia continued. "They're not going to meet us on a battlefield with a bunch of tanks, ... they're going to meet us in cyberspace. And from the attacks we're observing, I kind of dub 2017 the year of Iran."
-GoITWay
Google is making search engine more visual, intuitive; wants it to answer questions before being asked
Google unveiled changes Monday aimed at making the leading search engine more visual and intuitive to the point that it can answer questions before being asked.
Artificial intelligence and machine learning are core drivers of how Google will pursue its mission to organize the world's information and make it accessible to anyone, search vice president Ben Gomes said at an event in San Francisco.
The search engine focused strongly on mobile use and appeared to be growing more like Facebook, encouraging users to linger and explore topics, interests or stories with growing emphasis on photos and videos. Results will be increasingly personalised.
"Search is not perfect, and we are under no illusions it is," Gomes said.
"But, you have our commitment that we will make it better every day."
He described the latest changes as shifting from answers to journeys, providing ways to target queries without knowing what words to use and enhancing image-based searches.
Google Images was redesigned to weave in "Lens" technology that enables queries based on what is pointed out in pictures.
The Images overhaul includes carousels of online video clip highlights displayed with mobile search query results.
New Activity Cards will let users pick up searches where they left off, eliminating the need to retrace online steps.
The search engine will also let users create Collections of online content, and suggest related material that might be of interest.
A Google feed used by more than 800 million people monthly is getting a new name, Discover, and increased ability to offer people relevant information they are likely to want but haven't thought to ask for yet.
The feature was described as "Google search helping you discover new things without a query."

Google said it is also testing out an improvement to its job-related search results that will figure out what skills are needed for such posts and information about how to acquire them.
"Information and language are core to what we are as human beings," Gomes said.
"Our work here is never done."
Since being launched 20 years ago, Google has grown from simply a better way to explore the internet to an online tool so woven into daily life that its name has become a verb.
Early days of search were about software matching keywords or precise phrases to content on web pages, with typos or imprecise queries destined to fail.
Google has consistently refined its search algorithm, which it keeps secret, and uses AI to understand what people are looking for online and to tailor results based on what it knows about users individually and collectively.
Google's rise put it in the crosshairs of regulators, especially in Europe, due to concerns it may be abusing its domination of online search and advertising as well as Android smartphone operating software.

There have been concerns that parent company Alphabet is more interested in making money from people's data than in safeguarding their privacy.
Google was under fire anew from privacy advocates for a change that automatically signs users into Chrome browsers on desktop computers when they sign into any of the company's other services such as Gmail or search.
Chrome search data is not in sync with Google servers unless that function is enabled, the company said in an update to its policies.
Google is among the tech companies being called upon to better guard against the spread of misinformation - and has also been a target of US President Donald Trump, who added his voice to a chorus of Republicans who contend conservative viewpoints are downplayed in search results.
Google's anniversary also comes with the rising trend of people engaging with the internet through voice-commanded digital assistants, including one backed by the Silicon Valley giant.
Seattle-based Amazon last week sought to make its Alexa digital assistant and online services a bigger part of people's lives with an array of new products and partnerships.
Wednesday, 26 September 2018
WhatsApp says working with India's Reliance Jio to curb fake news menace
WhatsApp is working closely with Reliance Jio to spread awareness of false messages, weeks after the Indian telecoms operator opened up the messaging service to tens of millions of customers using its cheap internet-enabled phone.
Jio this month gave its more than 25 million JioPhone customers, many of them first-time internet users, access to WhatsApp at a time when the messaging service is battling false and incendiary texts and videos circulating on its platform.
Reliance Chairman Mukesh Ambani, India's richest man, launched the JioPhone last year at a refundable deposit of 1,500 rupees ($20.60). The device is internet enabled but didn't initially allow the use of WhatsApp or have several popular smartphone features.
All new users of the JioPhone get educational material that tells them about spotting a forwarded WhatsApp message and encourages them to share messages thoughtfully, WhatsApp spokesman Carl Woog told Reuters.
"We are working closely with Jio to continue our education campaign for WhatsApp users," Woog said.
In India's smaller towns and villages, deep-seated prejudices, often based on caste and religion, and cut-price mobile data can aggravate the so-called fake news problem. Such regions are a key market for cheap devices such as the JioPhone.
More than 30 people have died this year in mob violence triggered by vitriolic messages on social media and WhatsApp, according to unofficial estimates, and police have previously told Reuters that minorities have been targeted in some remote and rural regions.
That has prompted New Delhi to call on WhatsApp to take immediate action to "end this menace".
WhatsApp has already taken some steps to quell the rise of fake news. It has launched print and radio ad campaigns to educate users and introduced new features on the app including limiting message forwards as well as the labelling of forwarded messages.
It has also partnered with Digital Empowerment Foundation (DEF), a New Delhi-based non-profit organisation, to spread digital literacy in India's towns and cities.
DEF will host a workshop in the eastern Indian city of Ranchi this week, WhatsApp's Woog said.
WhatsApp also plans to expand its outreach programme to existing JioPhone users.
Reliance Jio did not immediately respond to an email seeking comment.
GOITWAY
Jio this month gave its more than 25 million JioPhone customers, many of them first-time internet users, access to WhatsApp at a time when the messaging service is battling false and incendiary texts and videos circulating on its platform.
Reliance Chairman Mukesh Ambani, India's richest man, launched the JioPhone last year at a refundable deposit of 1,500 rupees ($20.60). The device is internet enabled but didn't initially allow the use of WhatsApp or have several popular smartphone features.
All new users of the JioPhone get educational material that tells them about spotting a forwarded WhatsApp message and encourages them to share messages thoughtfully, WhatsApp spokesman Carl Woog told Reuters.
"We are working closely with Jio to continue our education campaign for WhatsApp users," Woog said.
In India's smaller towns and villages, deep-seated prejudices, often based on caste and religion, and cut-price mobile data can aggravate the so-called fake news problem. Such regions are a key market for cheap devices such as the JioPhone.
More than 30 people have died this year in mob violence triggered by vitriolic messages on social media and WhatsApp, according to unofficial estimates, and police have previously told Reuters that minorities have been targeted in some remote and rural regions.
That has prompted New Delhi to call on WhatsApp to take immediate action to "end this menace".
WhatsApp has already taken some steps to quell the rise of fake news. It has launched print and radio ad campaigns to educate users and introduced new features on the app including limiting message forwards as well as the labelling of forwarded messages.
It has also partnered with Digital Empowerment Foundation (DEF), a New Delhi-based non-profit organisation, to spread digital literacy in India's towns and cities.
DEF will host a workshop in the eastern Indian city of Ranchi this week, WhatsApp's Woog said.
WhatsApp also plans to expand its outreach programme to existing JioPhone users.
Reliance Jio did not immediately respond to an email seeking comment.
GOITWAY
Top practices for corporate users to optimize email security
Fortinet reminds corporate users in India that email remains one of the most vulnerable vectors targeted by cybercriminals. The cyber-attacks are likely to happen to organizations that have yet to implement strong email security controls and best practices.
According to the Verizon Data Breach Investigations report, two-thirds of installed malware are actually delivered by email. To gain access into an organization’s network, cybercriminals often use phishing or social engineering techniques in emails, thus counting on human error or a lack of cybersecurity know-how to trick users into providing login credentials or initiating fraudulent transactions, as well as to unknowingly install malware, ransomware and other malicious payloads.
“Due to the ubiquity of email, it continues to be a common attack vector for cybercriminals seeking to steal login credentials, money, and sensitive data.” Said Rajesh Maurya, Regional Vice President, India & SAARC, Fortinet. “The top email-based cyberattacks carried out by cybercriminals today include phishing or spear-phishing, man-in-the-middle attacks and zero-day vulnerabilities. Companies must therefore ensure they have strong security controls in place to detect and prevent these e-mail attacks.”
To help ensure email security, Fortinet’s cybersecurity experts advised users to:
Filter Spam. Because most email scams begin with unsolicited commercial email, one should take measures to prevent spam from getting into the mailbox. Most email applications and web mail services include spam-filtering features, or ways in which email applications can be configured to filter spam.
Regard Unsolicited Email with Suspicion. Don’t automatically trust any email sent by an unknown individual or organization. Never open an attachment to unsolicited email. Most importantly, never click on an unknown link in an email. Cleverly crafted links can take users to forged web sites set up to trick them into divulging private information or downloading viruses, spyware, and other malicious software.
Treat Email Attachments with Caution. Email attachments are commonly used by online scammers to sneak a virus onto computers. These viruses can help the scammer steal important information from the computer, compromising the computer so that it is open to further attack and abuse, and convert a computer into a ‘bot’ for use in denial-of-service attacks and other online crimes. As noted above, a familiar “from” address is no guarantee of safety because some viruses spread by first searching for all email addresses on an infected computer and then sending itself to these addresses.
Install Antivirus Software. Users should install an antivirus program that has an automatic update feature. This will help ensure users to always have the most up-to-date protection possible against viruses.
Install a Personal Firewall and Keep it Up to Date. A firewall will not prevent scam email from making its way into users’ mailbox. However, it may help protect users should they inadvertently open a virus-bearing attachment or otherwise introduce malware to their computer. The firewall, among other things, will help prevent outbound traffic from a user’s computer to the attacker. When a personal firewall detects suspicious outbound communications from a user’s computer, it could be a sign that the user has inadvertently installed malicious programs on his computer.
According to the Verizon Data Breach Investigations report, two-thirds of installed malware are actually delivered by email. To gain access into an organization’s network, cybercriminals often use phishing or social engineering techniques in emails, thus counting on human error or a lack of cybersecurity know-how to trick users into providing login credentials or initiating fraudulent transactions, as well as to unknowingly install malware, ransomware and other malicious payloads.
“Due to the ubiquity of email, it continues to be a common attack vector for cybercriminals seeking to steal login credentials, money, and sensitive data.” Said Rajesh Maurya, Regional Vice President, India & SAARC, Fortinet. “The top email-based cyberattacks carried out by cybercriminals today include phishing or spear-phishing, man-in-the-middle attacks and zero-day vulnerabilities. Companies must therefore ensure they have strong security controls in place to detect and prevent these e-mail attacks.”
To help ensure email security, Fortinet’s cybersecurity experts advised users to:
Filter Spam. Because most email scams begin with unsolicited commercial email, one should take measures to prevent spam from getting into the mailbox. Most email applications and web mail services include spam-filtering features, or ways in which email applications can be configured to filter spam.
Regard Unsolicited Email with Suspicion. Don’t automatically trust any email sent by an unknown individual or organization. Never open an attachment to unsolicited email. Most importantly, never click on an unknown link in an email. Cleverly crafted links can take users to forged web sites set up to trick them into divulging private information or downloading viruses, spyware, and other malicious software.
Treat Email Attachments with Caution. Email attachments are commonly used by online scammers to sneak a virus onto computers. These viruses can help the scammer steal important information from the computer, compromising the computer so that it is open to further attack and abuse, and convert a computer into a ‘bot’ for use in denial-of-service attacks and other online crimes. As noted above, a familiar “from” address is no guarantee of safety because some viruses spread by first searching for all email addresses on an infected computer and then sending itself to these addresses.
Install Antivirus Software. Users should install an antivirus program that has an automatic update feature. This will help ensure users to always have the most up-to-date protection possible against viruses.
Install a Personal Firewall and Keep it Up to Date. A firewall will not prevent scam email from making its way into users’ mailbox. However, it may help protect users should they inadvertently open a virus-bearing attachment or otherwise introduce malware to their computer. The firewall, among other things, will help prevent outbound traffic from a user’s computer to the attacker. When a personal firewall detects suspicious outbound communications from a user’s computer, it could be a sign that the user has inadvertently installed malicious programs on his computer.
Friday, 21 September 2018
Over 30Bn malicious login attempts detected under 1 year: Akamai report
Cloud delivery network provider Akamai Technologies has detected 30 billion malicious login attempts globally during a period of eight-months ending in June 2018, the company has said in a new report.
In the report titled "Akamai 2018 State of the Internet/Security Credential Stuffing Attacks", the company said it detected around 3.2 billion malicious logins per month from January through April 2018, and over 8.3 billion malicious login attempts from bots in May and June 2018.
The financial services industry bears the major burden of such attacks. The report combines attack data from across Akamai's global infrastr. cture and represents the research of a diverse set of teams throughout the company.
Malicious login attempts result from credential stuffing, where hackers systematically use botnets to try stolen login information across the web. They target login pages for banks and retailers on the premise that many customers use the same login credentials for multiple services and accounts.
Credential stuffing can cost organisations millions to tens of millions of dollars in fraud losses annually.
Infosys to open tech hub in Arizona, to hire 1000 people by 2023
Infosys said it would open its technology and innovation hub in Arizona and would hire 1000 people in the stately 2023.
The Arizona hub will focus on autonomous technologies, Internet of Things (IOT), full-stack engineering, data science and cyber security.
In May 2017, Infosys had said it would hire 10,000 American workers and the company said that it has 5874 workers so far.
“This investment will strengthen our ability to deliver for our clients across Arizona and the Southwest and expand the local workforce to help our clients compete in the rapidly digitizing global economy,” said Ravi Kumar, President, Infosys
To date, Infosys has opened two US technology hubs, one in Indianapolis, Indiana and another in Raleigh, North Carolina. Infosys has also announced that it will build hubs in Hartford, Connecticut and Providence, Rhode Island.
State governments fast embracing AWS Cloud in India: Teresa Carlson
When it comes to Cloud adoption, state governments in India are quickly shifting their workloads to the platform -- even faster than the US state governments, said a top executive from Amazon Web Services (AWS).
According to Teresa Carlson, Vice President, Worldwide Public Sector at AWS, in just about two years, there has been a significant change on Cloud adoption in the public sector in India.
"When I first visited India in 2016, people, although tech savvy, were not much exposed to Cloud computing and capabilities it brings in. Startups were always enthusiastic but within the government circles, the buzz around Cloud was just shaping up," Carlson told IANS during a free-wheeling interview.
"On my second India visit, I am glad to see the transformation. They are now clearly aware about Cloud computing and immense benefits associated with it," she emphasised.
According to Teresa Carlson, Vice President, Worldwide Public Sector at AWS, in just about two years, there has been a significant change on Cloud adoption in the public sector in India.
"When I first visited India in 2016, people, although tech savvy, were not much exposed to Cloud computing and capabilities it brings in. Startups were always enthusiastic but within the government circles, the buzz around Cloud was just shaping up," Carlson told IANS during a free-wheeling interview.
"On my second India visit, I am glad to see the transformation. They are now clearly aware about Cloud computing and immense benefits associated with it," she emphasised.
Wednesday, 19 September 2018
A new AI solution released by Dell EMC for digital transformation
Dell EMC announces new solutions to help organisations realise the full potential of Artificial Intelligence (AI).

Dell EMC on Tuesday announced new solutions that are designed to simplify the AI environment and accelerate its adoption. This has been done in order to help organisations realise the full potential of Artificial Intelligence (AI).
With the new "Ready Solutions for AI", organisations no longer have to individually source and piece together their own solutions, Dell EMC said in a statement.
Instead, they can rely on a Dell EMC-designed and validated a set of best-of-breed technologies for software - including AI frameworks and libraries - with computer, networking and storage, the company added.
Dell EMC said its portfolio of services, including consultation, deployment and support, among others, helps customers drive the rapid adoption and optimisation of their AI environments.
"There's no doubt that AI is the future, and our customers are preparing for it now," said Tom Burns, Senior Vice President, Networking and Solutions, Dell EMC.
"Our goal is to lead the industry with the most powerful and fully-integrated AI solutions. What we're announcing today allows customers at any scale to start seeing better business outcomes and positions them for AI's increasingly important role in the future," Burns added.
According to an IDC estimate, 40 per cent of digital transformation initiatives will use AI services by 2019.
The new AI solutions from Dell EMC come with specialised designs for Machine Learning (ML) with Hadoop, an ecosystem of open source components, and Deep Learning with Nvidia, a US-based computer chip manufacturer.
Dell EMC, a part of Dell Technologies, enables organisations to modernise, automate and transform their data centre using industry-leading converged infrastructure, servers, storage and data protection technologies.
(With IANS inputs)
-GoITWay
Apple: New iOS 12 comes with new tools, now available globally

The Apple's iOS 12 is now available globally. This is the latest version of the advanced mobile operating system (OS) that is said to make daily tasks faster and more responsive.
The new OS will bring performance improvements across the system, including the previous version i.e supporting iPhone 5s, which was introduced in 2013.
"Available as a free software update, iOS 12 introduces new augmented reality (AR) experiences, fun new features like Memoji, Siri Shortcuts that open up a world of apps to work with Siri and new tools to help people reduce interruptions and manage screen time for themselves and their families," the iPhone maker said in a statement late on Monday.
The Cupertino-based giant said with iOS 12, camera launches up to 70 per cent faster, the keyboard appears up to 50 per cent faster and typing is more responsive.
"When there is a lot going on across the system, apps can launch up to twice as fast," the company added.
A few new tools like "Screen Time" built into the iOS 12 help users understand and take control of the time they spend interacting with their devices.
This feature provides users with detailed information and tools to help them manage the time they spend with apps and websites and better understand and control where their child spends time.
Another nifty addition is "Siri Shortcuts" that allows any app to now work with Apple's digital assistant Siri.
With powerful on-device intelligence, Siri learns user routines and provides suggestions at just the right time.
"Users can also use their voice to run any shortcut, making it even easier to use their favourite apps. The new shortcuts app goes even further, allowing users to create custom shortcuts to streamline frequent tasks," the company said.
(With IANS inputs)
-GoITWay
Tuesday, 18 September 2018
Cloud complexity management is the next big thing
Where have you heard that enterprises using cloud are moving to more complexity as well? That’s right, from this guy.
The growing cloud computing complexity was recently documented by the Wall Street Journal that cites a survey of 46 CIOs by KeyBanc Capital Markets. It found that 32 percent said they plan to use multiple vendors to create internal private cloud systems, while 27 percent planned hybrid cloud arrangements.[ IDG Research: The state of the cloud: How enterprise adoption is taking shape. | Keep up with the latest developments in cloud computing with InfoWorld’s Cloud Computing newsletter. ]
Companies “increasingly are going to employ multiple clouds, a hybrid of public and private, which is driving increased complexity in IT environments, full stop,” said Alex Kurtz, a senior analyst with KeyBanc.
No, I’m not writing this post to gloat (I’ll do that on social media). I’m trying to raise awareness that cloud complexity is something that’s inevitable. However, it’s also something that can be managed—that is, if you’re proactive enough and willing to put some resources on it.
Traditional thinking is that cloud computing will replace hardware and software systems, so things will be simpler. You’ll just have to spend a few days moving workloads and data using processes so easy that the applications and data almost migrate themselves.
But it turns out to be a complex migration process with many new choices to make and new technology to use. Where you once had five security systems, you now have 20. Where you had three directories, you now have seven.
Why? It turns out you cannot just shut down the old stuff, so the hardware, software, and supporting systems remain. At the same time, you are standing up cloud-based systems that used a whole new set of skills and technology. Thus the complexity.
There are a few choices that you can make to manage this process:
You can choose to not go to cloud, but that’s a death sentence for IT.
You can hire three times the people and toss money at the problem.
You can learn to effectively manage the complexity, and even make things less complex with the addition of cloud computing.
For those of you who want to see what’s behind door No. 3, it involves a bunch of upfront planning. The upfront plan must deal with security, governance, data, applications, ops, etc., and place them within manageable domains. You use abstractions to simplify the management, which includes combining traditional systems and cloud systems’ patterns in domains.
This discipline is called cloud complexity management, or CCM. You’ll be hearing more about it later this year and in 2019. Best get the religion now, before it’s too late.
-GoITWay
Subscribe to:
Comments (Atom)